Prerequisites
Before you can deploy Ververica Cloud: Bring Your Own Cloud, you must meet the prerequisites and environment setup such as configuring S3 buckets. By doing so, you ensure proper OpenID Connect (OIDC) integration and create necessary IAM roles and policies. Verify the following prerequisites:
- Infrastructure and Compatibility
- Capacity (Sizing) Requirements
- Network Access Requirements
- Identity and Access Management (IAM) Requirements
These requirements apply to both the Ververica agent and the workspaces it manages.
Infrastructure and Compatibility Requirements
Ensure your setup meets the supported infrastructure requirements and verify IMDSv1 is available on your worker nodes.
| Requirement | Specification |
|---|---|
| Kubernetes Distribution | EKS |
| Kubernetes Version | ≥ 1.28 |
| EKS Deployment Type | EC2 |
| EC2 Operating System | Linux |
| EC2 Instance Families | m5, m6, m5.metal, etc. |
| Supported Storage Class | gp2, gp3 |
Amazon EKS
If you are deploying on Amazon EKS, ensure that IMDSv1 is enabled on your EC2 worker nodes.
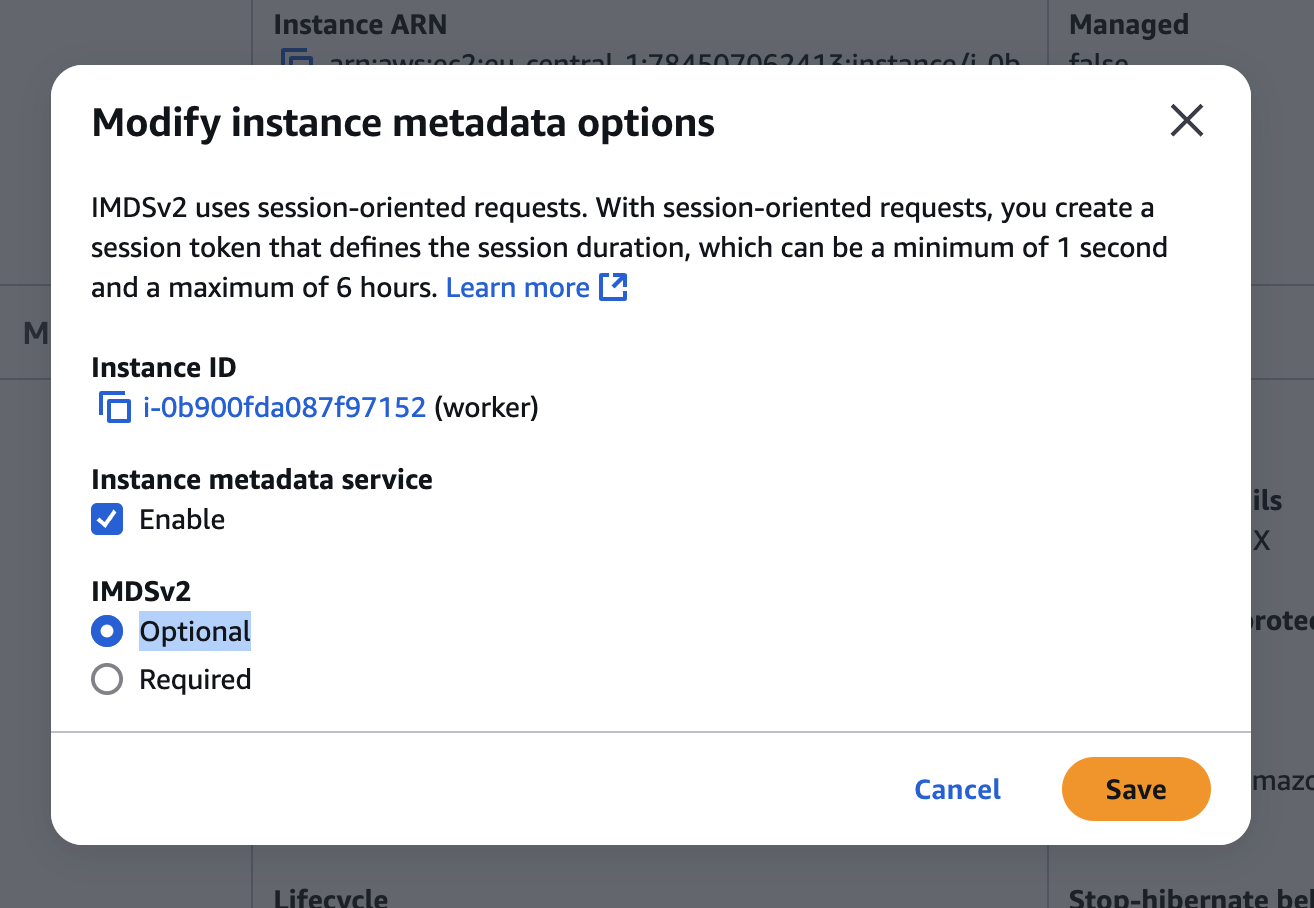
Note: Currently, the Ververica Agent requires IMDSv1 access. If IMDSv2 is set to Required (disabling IMDSv1), the Agent will fail to initialize and produce 401 errors when running in EKS.
Verify each instance’s IMDSv2 metadata options are set to Optional.
- Open Actions → Instance Settings → Modify instance metadata options in the Amazon EC2 console.
- Under IMDSv2, choose Optional.
- Save the changes.
If your EKS cluster creates additional worker nodes automatically, be sure to update the nodegroup launch configuration or template to enable IMDSv1 for new nodes.
Capacity (Sizing) Requirements
Ensure your capacity meets the minimum requirements.
| Requirement | Specification |
|---|---|
| Persistent Volume Claims (PVC) Per Workspace | 2 PVCs per workspace |
| PVC Capacity | 5 GB per volume |
| Network Security Policy | Allow outbound traffic to app.ververica.cloud |
| Pod CPU Requests (Per Workspace) | 3 vCPU per workspace |
| Pod Memory Requests (Per Workspace) | 18 GB per workspace |
| Agent Components CPU/Memory (Combined) | 2 vCPU, 4 GiB memory (limits) |
Network Requirements (Whitelisting)
If your cluster or network environment restricts outbound traffic by default (for example, through DNS filtering, firewall rules, or a proxy), you must explicitly allow HTTPS egress and DNS resolution for the following domains:
agent.ververica.cloud- communicates with the Ververica Control Planeapp.ververica.cloud- allows each workspace’s console agent to connectregistry.ververica.cloud- pulls container images for Agent componentscdn.ververica.cloud- downloads Flink engine artifacts
If access to these endpoints is blocked or is not resolvable via DNS, the Ververica agent will remain pending and fail to register.
Note: You do not need to allow all outbound traffic. Instead, you can add specific rules or allowlists to permit HTTPS connections only to these required domains. This approach maintains a more restricted security posture while still enabling the Ververica Agent and its components to function.
IAM Requirements
If you are not using the CloudFormation script, ensure you have set up the correct IAM roles, permissions, and S3 bucket configurations.
If you are using the CloudFormation script, proceed to creating AWS resources.