Secret Values
Secret Values may be used to store sensitive information such as passwords, tokens or keys. While Secret Values are referenced by name in Deployment specifications, their actual values are not exposed to users.
Secret Values are bound to a Namespace. Within each Namespace the names of the Secret Values have to be unique.
Secret Values Specification
Plain Secret Values
Plain Secret Values are persisted in plain text within the context of Ververica Platform. They simply provide a value containing the secret.
kind: SecretValue
metadata:
name: SECRET_VALUE_NAME
namespace: default
...
spec:
kind: PLAIN
value: secret
Using Secret Values
Secret Values may be referenced by name in configurations using ${SECRET_VALUE_NAME}.
Secret Values are only allowed on the following Deployment Template configuration fields:
- Jar URI (
spec.template.artifact.jarUri) if the Artifact is of kindJAR - Apache Flink® Configuration (
spec.template.flinkConfiguration)
When referencing Secret Values curly braces ${} are mandatory.
Secret values for Connectors & Catalogs
Secret values are enabled in SQL scripts and catalogs, enhancing security of sensitive information when passing credentials to connectors. Additionally, the centralized management and storage of secret values promotes consistency and credential reusability across teams.
Secret values can be accessed and created from the Administration menu under Secret Values.
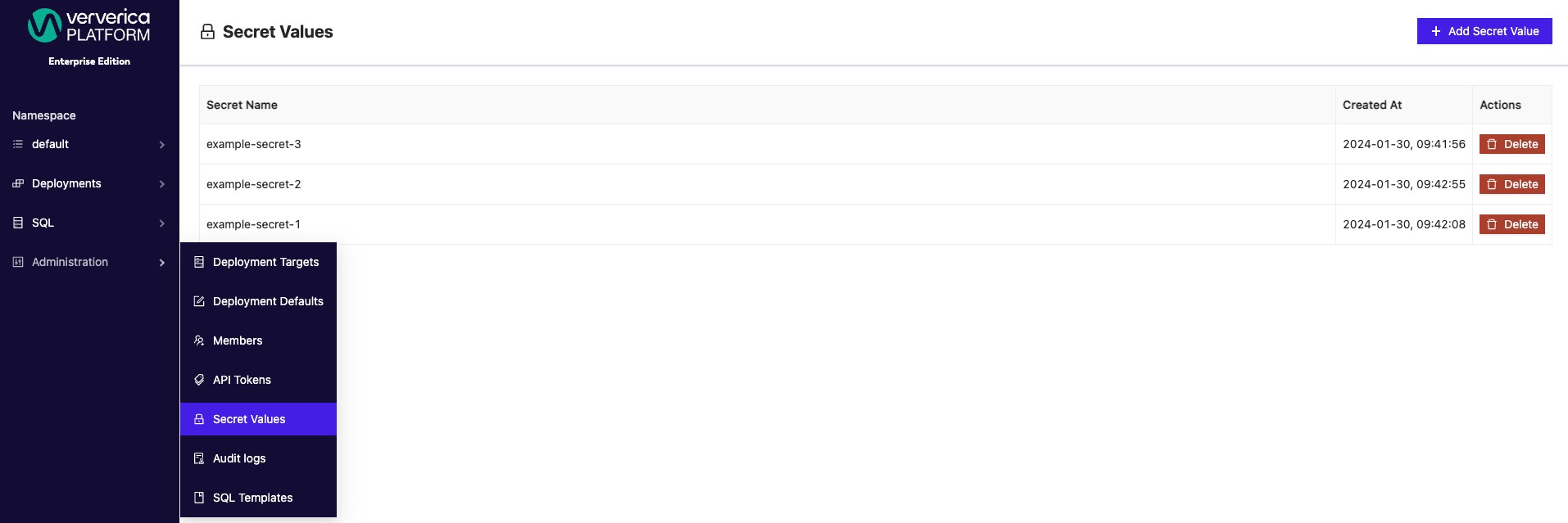
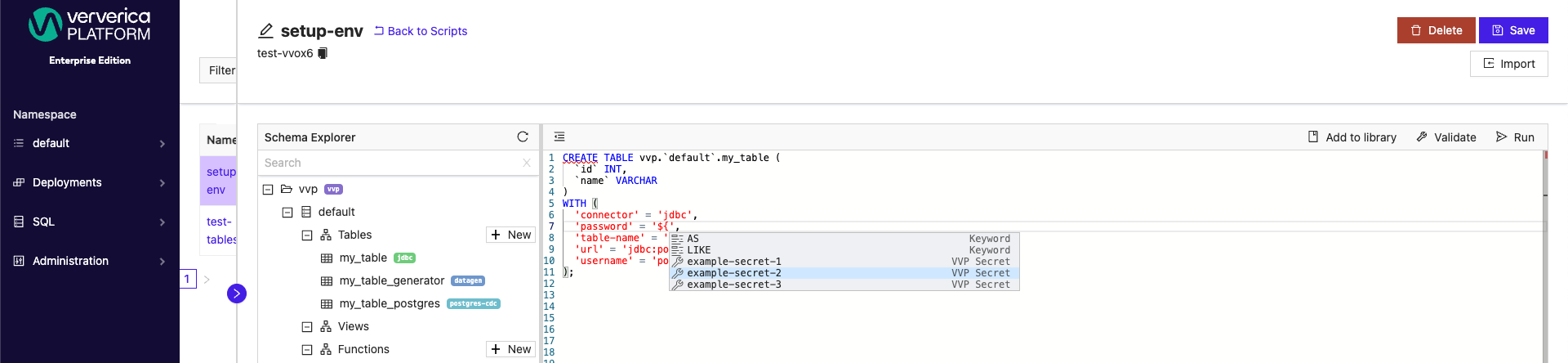
When creating a new secret value, the syntax required is your secret name wrapped inside ${}. For example, ${example-secret}. Configured secrets can be applied as Default Values for both catalogs and connectors from the SQL menu. Secrets can be applied to both new and existing catalogs.
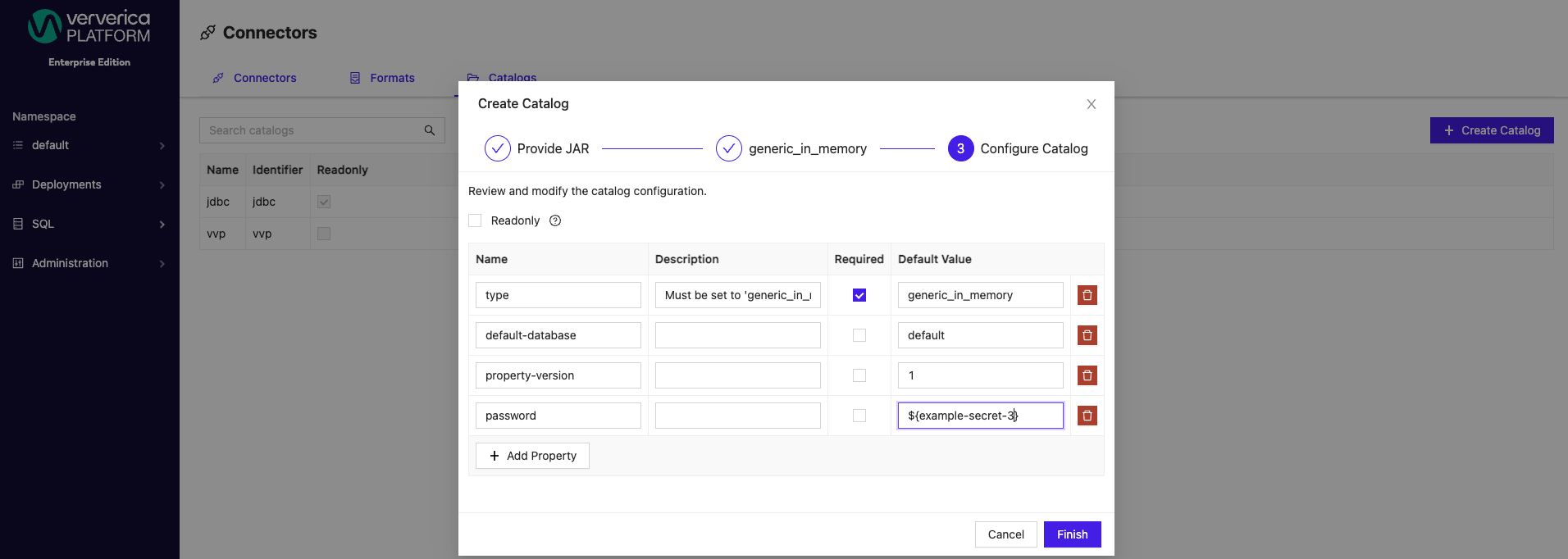
Similarly, for connectors, secrets can be applied to both new and preexisting connectors.
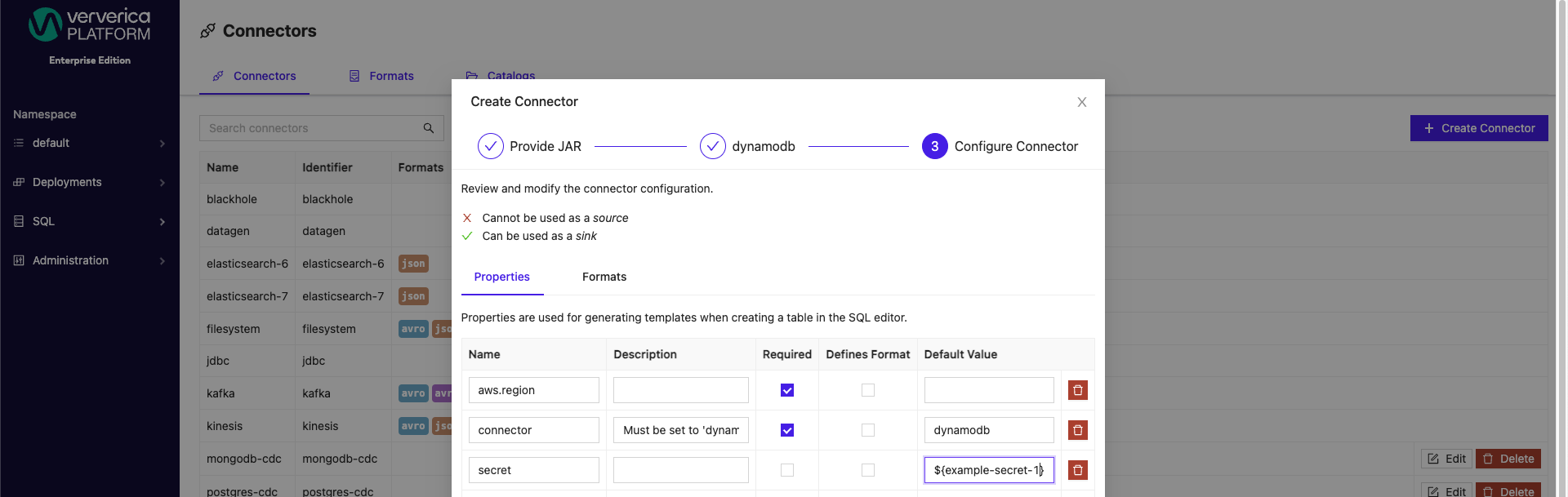
SQL Scripts can also have secret values applied when creating new or updating existing catalogs.
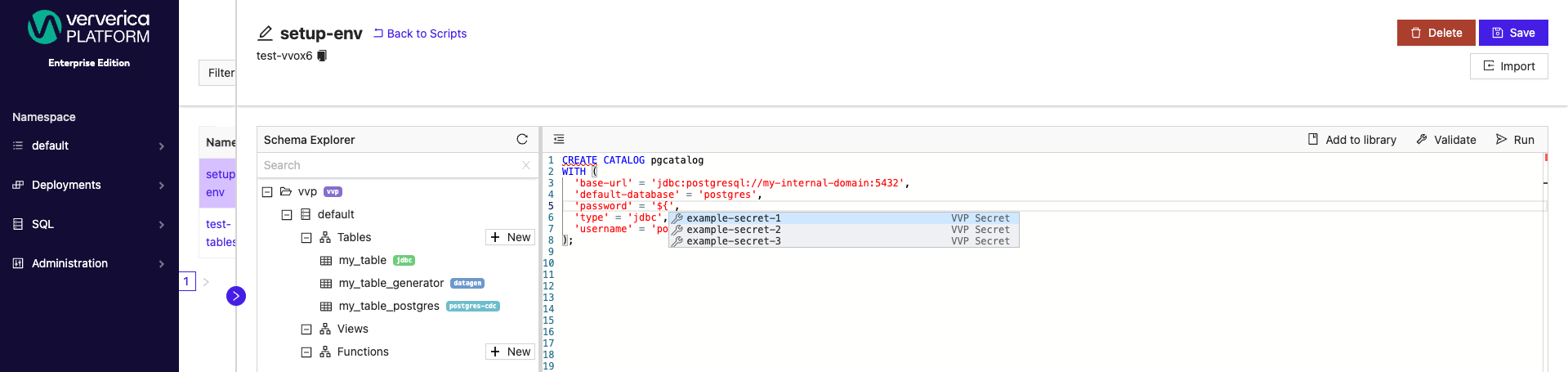
Additionally, new and existing tables can have secret values applied.
 .
.
In the SQL Scripts window you can use autocomplete mechanism (typically CTRL + Space) to display and choose one of existing secret names.
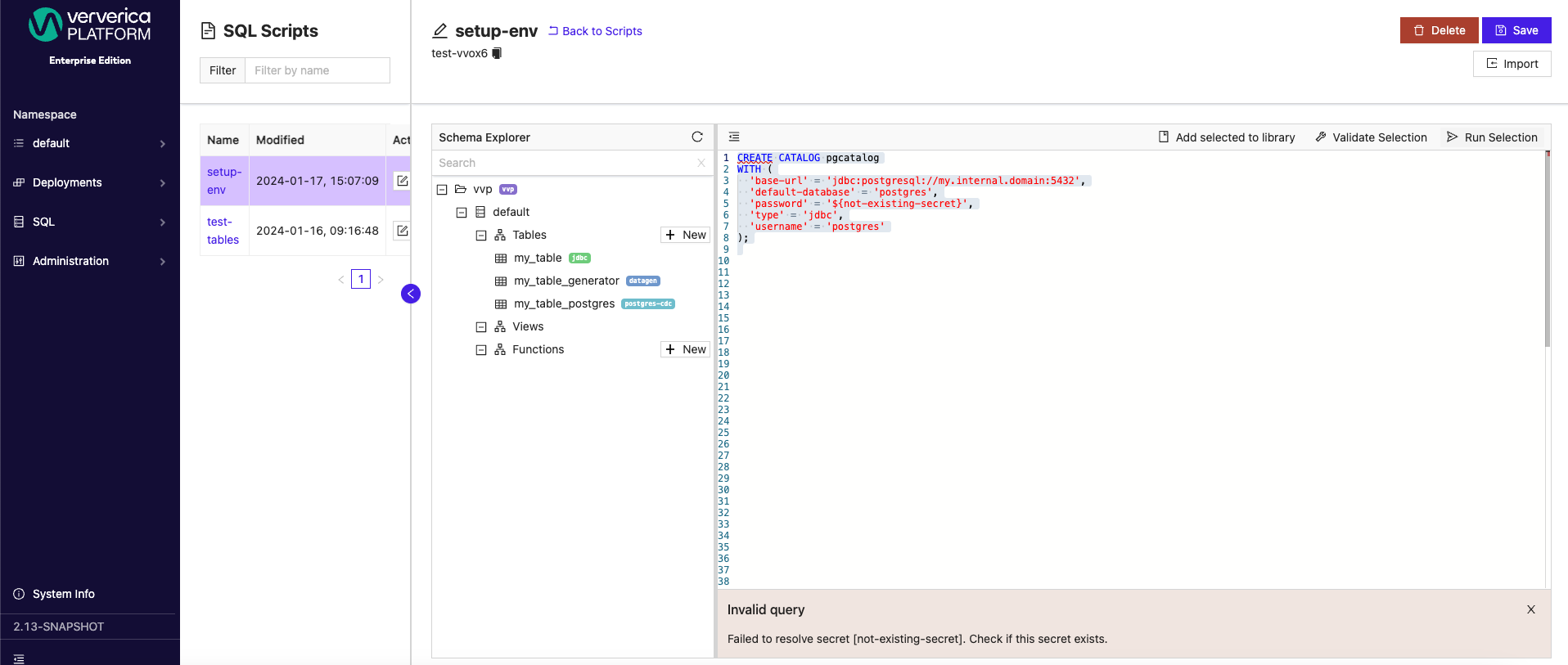
Before using a placeholder, make sure that the secret with the selected name is already created. If it does not exist, validation of the operation will fail like in the example image below.
 .
.
The Ververica distribution of Apache Flink® does not include any special precautions for protecting access to secrets. Secret Values may be exposed on the Flink UI and Kubernetes ConfigMaps. Make sure to restrict access to the Kubernetes cluster and to the Flink UI.