Ververica Cloud: Bring-Your-Own-Cloud (BYOC)
Ververica Cloud Bring-Your-Own-Cloud provides a managed experience with the user’s own cloud resources.
Fundamentals
This page outlines the fundamentals of Ververica Cloud Bring Your Own Cloud (BYOC). It describes the design, benefits, and the shared responsibility model.
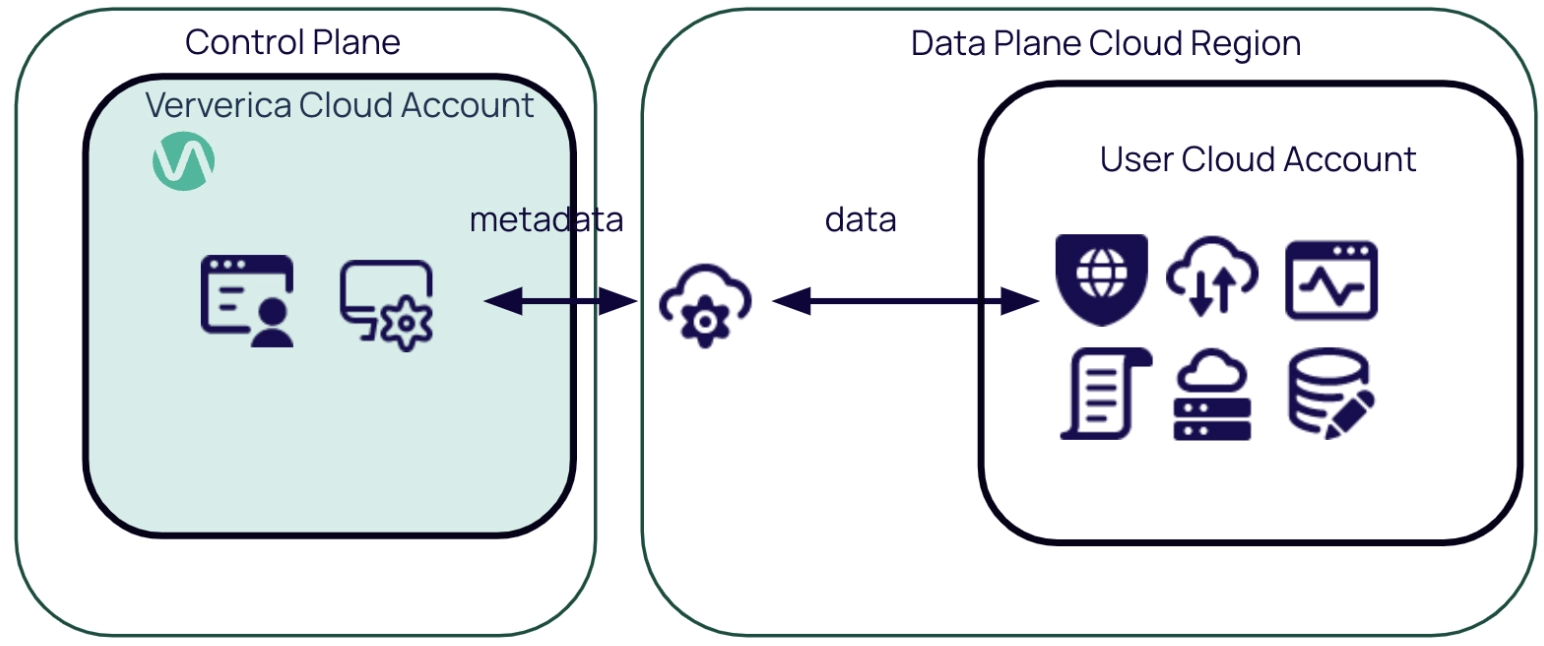
The BYOC deployment model revolves around the separation between the following:
- Central control plane residing in Ververica Cloud
- Distributed data plane residing in User Cloud(s).
Control plane
- The central control plane is hosted in a Ververica Cloud account, fully managed by Ververica and publicly accessible through load balancing mechanisms.
- Users can control all BYOC tenant workspaces through a single pane of glass over the control plane.
- Only metadata is stored in Ververica Control Plane and transferred between control and data planes.
Data plane
- The data plane is distributed as a set of Ververica cloud native microservices, deployed in the User Cloud Account using User Cloud Resources.
- User data is stored in the user cloud, completely controlled by the user.
O- n the data plane, each BYOC tenant workspace created by the user is handled by a separate agent, platform and engine services. - Data plane artifacts are deployed as containers orchestrated by Kubernetes container orchestration.
- Each tenant workspace is attached to dedicated object storage for user data provided by the user. Ververica manages data in this object storage instance, based on object storage API level (least-privilege) access policies.
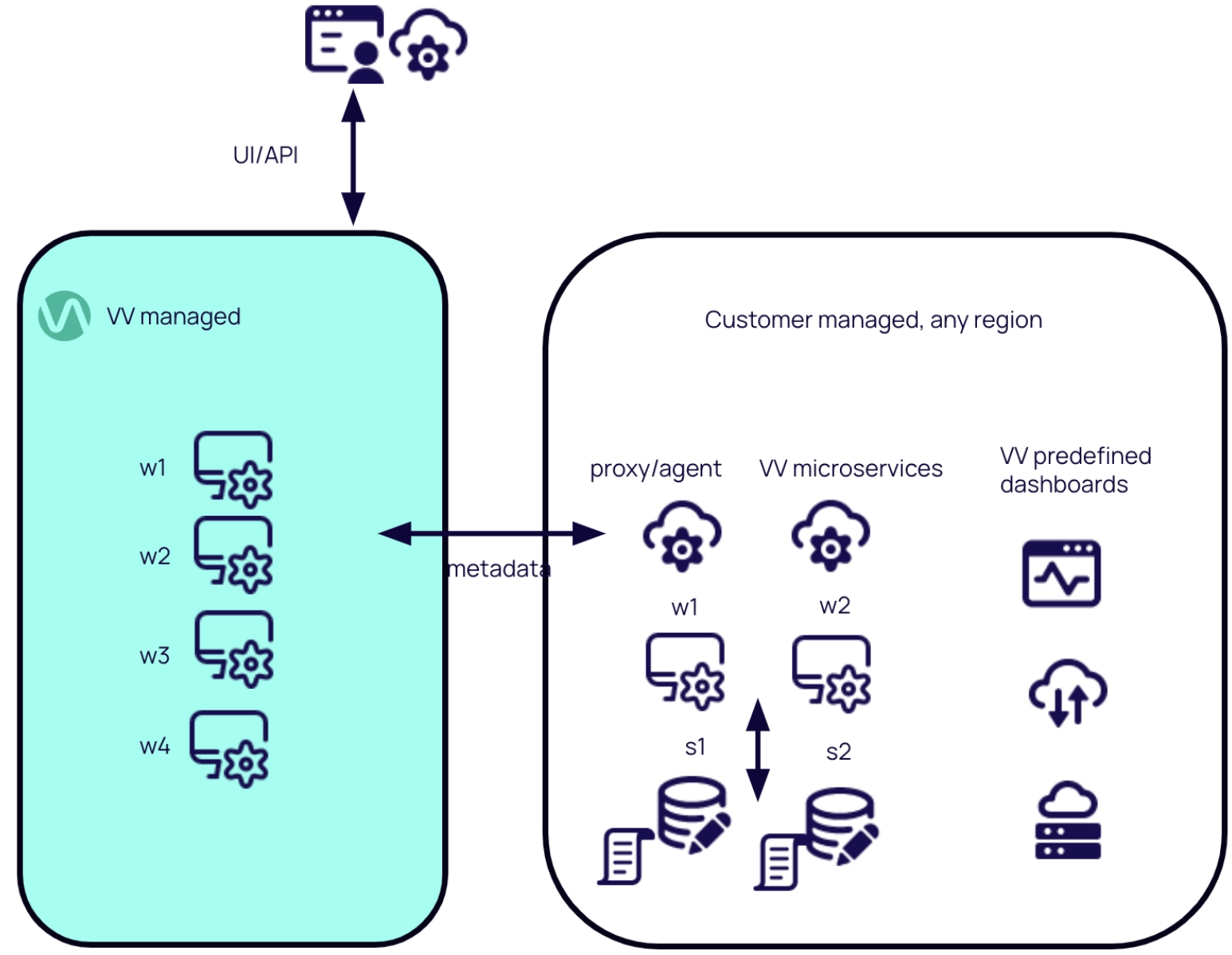
Agent services
The agent's primary role is to establish client connection from, and manage Veverica platform services in, the User cloud.
- The agent establishes a client connection from the user cloud to Veverica Cloud, which allows users to have full control and observability.
- An agent may handle one or more BYOC tenant workspaces.
- An agent is an umbrella for a set of cloud-native microservices such as API Gateway, Controller, Webhook, and Manager, each performing a separate function in a decoupled manner.
- Agent services are managed by customers via helm/kubectl tooling.
Platform services
-
Platform services are responsible for managing Veverica platform tenant workspaces with consoles.
-
Platform services are managed through the control plane, centrally.
VERA engine
VERA engine artifacts are responsible for providing the runtime VERA engine for deployment or session cluster jobs.
Zero trust first design
Veverica BYOC is built using zero trust first design principles.
That means that BYOC is built on a least-privilege model, identity-based authentication, separation of concerns, fine-grained authorization policies, short-lived credentials, where the User controls security policies and has full observability.
The user manages and is in full control of infrastructure cloud resources, services and integrations, while Ververica manages its own cloud-native services.
Benefits
- Leverage user’s cloud partnerships cost savings
- Data sovereignty (data is in the user's cloud)
- Retain tenancy at workspace level for cost optimized separation of concerns
- Zero trust model
- No cloud vendor or region lock-in
- Pay-as-you-go, capacity-based offering
- Broad accessibility over public Internet
- Marketplace offering, one bill
This is a shared responsibility model with a fully managed control plane. The Ververica data plane containers reside in the user’s cloud account, part of the user's managed cloud resources.
BYOC: Shared responsibility model
Ververica fully manages the control plane
Ververica responsibility:
- Ververica fully manages the control plane, and metadata in the control plane.
- Distribution of data plane cloud-native agent, platform and engine containers with agent helm charts.
- Management of metadata in the control plane, data in the user data plane, releases and life cycle of Ververica cloud-native services.
User manages:
- Ververica agents
- All infrastructure (EKS, EC2, VPC etc.)
Targeting zero trust – requirements:
- Ververica agents via helm / kubectl tooling.
- All required infrastructure and 3rd party services (Storage, Networking, Compute, Metrics and Logging systems, etc.)