About Ververica Cloud: Bring Your Own Cloud
The Ververica Cloud: Bring Your Own Cloud (BYOC) deployment option enables organizations to run Apache Flink workloads within their own Kubernetes environment while maintaining centralized control through the Ververica Cloud Control Plane. This model ensures organizations retain data residency, security, and compliance requirements while leveraging Ververica’s fully-managed Flink experience.
Is BYOC the Right Option for You?
Ververica’s BYOC deployment is ideal for enterprises that:
- Want to retain full control over their cloud infrastructure.
- Prefer or require full observability of their data.
- Have specific security, governance, or compliance needs.
- Are adopting a zero-trust security strategy.
- Use multi-cloud or hybrid cloud architectures.
- Have preferential pricing or spend commitments with cloud providers.
- Need a flexible, scalable solution for real-time stream processing.
- Want to leverage (VERA), the engine revolutionizing Apache Flink for their streaming and batch processing projects, and will benefit from a managed Flink offering within their own cloud environment.
Architecture
The BYOC architecture consists of two primary components: the Control Plane and Data Plane.
Control Plane (Managed by Ververica)
- Hosted in Ververica Cloud.
- Provides a centralized interface for managing Flink deployments, monitoring, and configuration.
- Sends instructions and manages workloads running in customer clusters.
Data Plane (Customer-Managed Kubernetes Cluster)
- Runs Flink workloads within the customer’s infrastructure.
- Communicates securely with the Control Plane.
- Operates in compliance with the customer's security and network policies.
The image below illustrates these components and highlights the security and operational framework of Veverica's BYOC deployment model. The VERA engine serves as the runtime for deployment or session cluster jobs.
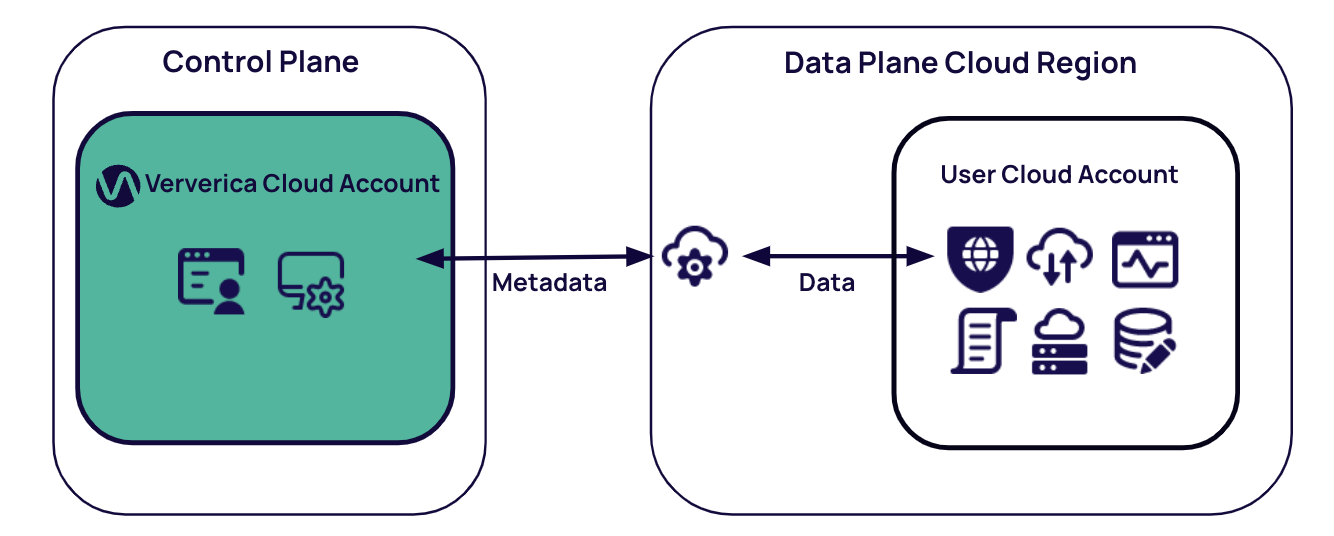
For more information, see How BYOC Works.
Security & Compliance
Ververica Cloud: Bring Your Own Cloud follows zero-trust principles, ensuring full control over security policies and observability. Key security features include:
- Limits permissions to minimize security risks through least-privilege access.
- Grants access only to verified users and systems with identity-based authentication.
- Segments infrastructure to reduce security impact with isolation.
- Defines detailed access controls for resources with fine-grained authorization.
- Limits exposure with temporary access tokens using short-lived credentials.
- Enables customization of security policies and compliance measures with user-controlled security.
- Provides visibility into system performance and security with full observability.
For more information, see BYOC Security Model.
Operational Responsibilities
The BYOC deployment option uses a shared responsibility model. All data processing and data movement happens within the customer cloud (inside the customer cloud account), keeping processing and data movement local and entirely under your control. You manage and are in full control of infrastructure cloud resources, services and integrations, while Ververica manages its own cloud-native services.
The image below depicts the separation of responsibilities. Ververica manages the control plane. Customers manage the data plane.
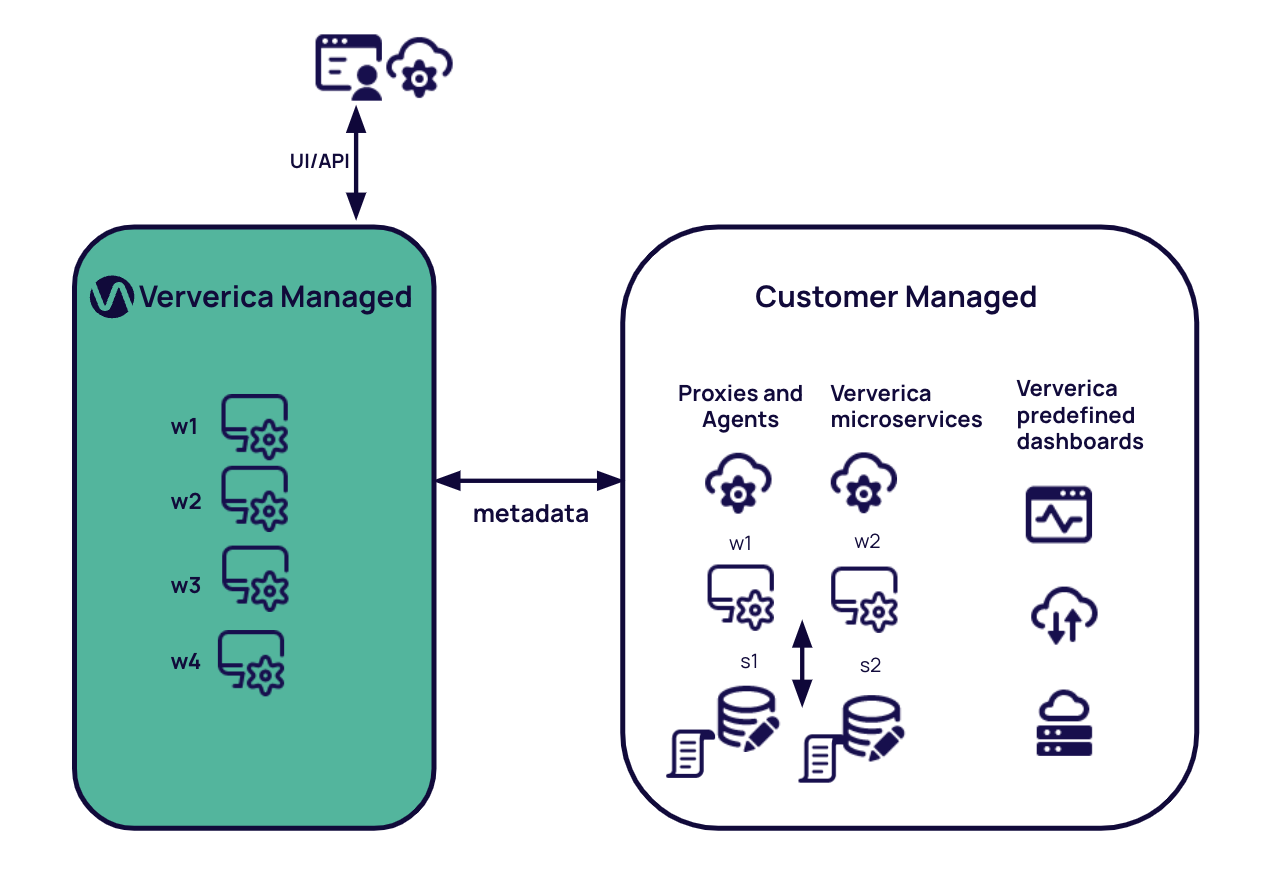
Ververica Responsibilities
Ververica is responsible for maintaining and managing key components of the deployment framework to ensure seamless operations and integration with customer infrastructure. Ververica oversees cloud-native services and supports customers by reducing operational complexity and maintaining high availability. The responsibilities include:
- Managing and distributing agent, platform, and engine containers via helm charts.
- Maintaining metadata in the control plane and overseeing lifecycle updates to Ververica services.
- Ensuring smooth integration and lifecycle management of cloud-native services.
Customer Responsibilities
Customers maintain a high degree of operational responsibility for the underlying infrastructure and service integrations within their own cloud environments. While Ververica manages essential cloud-native services and operational tasks, customers are fully accountable for managing their own resources, configuring their environment, and ensuring compliance with their organizational security and operational standards. The responsibilities include:
- Managing cloud infrastructure (e.g., EKS/AKS, EC2/VMs, VPC/VNet, etc.).
- Setting up and maintaining compute instances, storage, networking, metrics, and logging systems.
- Managing services and integrations, including custom requirements.
- Implementing zero-trust security policies, including agent configuration.
Responsibility Matrix
The matrix below summarizes these responsibilites.
| Responsibility | Customer | Ververica |
|---|---|---|
| Manage Kubernetes cluster | ✅ | ❌ |
| Deploy and maintain Flink workloads | ✅ | ❌ |
| Control Plane operations | ❌ | ✅ |
| Flink version updates & patches | ✅ | ✅ (control layer) |
| Security & access controls | ✅ | ✅ (agent & API security) |
| Observability & monitoring | ✅ | ✅ (UI-level insights) |
Key Benefits
- Optimize spend by using existing cloud spend agreements or credits without incurring additional costs for vendor lock-in. Pay only for what is used with a pay-as-you-go, capacity-based pricing structure.
- Implement a zero-trust security architecture with fine-grained access controls so teams can fully define encryption, access policies, and data handling tailored to their security posture.
- Switch or scale vendors across cloud regions as business priorities shift without rebuilding entire environments. Avoid vendor or regional lock-in with flexible, multi-cloud options.
- Ensure adherence to strict regulatory requirements by keeping data within your cloud environment. Retain logical tenancy at the workspace level to enable cost-optimized separation of business concerns.
- Benefit from marketplace integration with a single, consolidated billing approach. Access the platform securely over the public internet while maintaining compliance and security policies.
Get Started
Getting started with Ververica Cloud: Bring Your Own Cloud (BYOC) is simple and fast. In a few steps, you’ll deploy the Ververica Agent on your Kubernetes cluster, connect it to the Ververica Cloud Control Plane, and start creating workspaces in your own cloud environment.
Go to Getting Started to learn how to get up and running with Ververica Cloud: Bring Your Own Cloud, and go to Ververica Unified Streaming Data Platform interface to learn how to get the most value from it.