Pluggable Certificates
You can use your own certificates to enable SSL for Flink internal/external communications, via the following steps
- Generate Certificates for VVP and Flink Jobs
- Provide deployment with custom ssl Flink Configuration
- Provide configuration for VVP installation with custom keystore
Configuration
In order to begin using certificates for Flink internal and external communications, users will have to follow several configuration steps including generating keystores, Kubernetes environment preparation, SSL enablement, and finally deployment.
The commands in the following sections generate a keystore:
- For Ververica Platform:
vvp.keystore - For a Flink job
flink-rest.keystore - For Result Fetcher service:
result-fetcher-rest.keystore
If you want to use your own public/corporate CA signed certificate, please ask your security team to generate the three keystores by following the similar procedure.
The procedure below uses two Kubernetes namespaces:
vvp-namespace: the Kubernetes namespace where Ververica Platform runsjob-namespace: the Kubernetes namespace where Flink jobs and Result Fetcher service run
Substitute them with the namespaces you use in your own Kubernetes cluster if necessary.
Generate Ververica Platform keystore
In order to genereate the keystore for Ververica Platform appmanager, use the following commands:
keytool -genkeypair -alias rootca/v2 -dname "cn=ca.app-manager.v2" -validity 10000 -keyalg RSA -keysize 4096 -ext "bc=ca:true" -ext KeyUsage:critical=keyCertSign -keystore vvp-root.keystore -keypass key-store-pass -storepass key-store-pass
keytool -exportcert -keystore vvp-root.keystore -alias rootca/v2 -storepass key-store-pass -file vvp-root.cer
keytool -genkeypair -alias client -dname "cn=me.app-manager" -validity 10000 -keyalg RSA -keysize 4096 -keystore vvp-client.keystore -keypass key-store-pass -storepass key-store-pass
keytool -exportcert -keystore vvp-client.keystore -alias client -storepass key-store-pass -file vvp-client.cer
keytool -importkeystore -srckeystore vvp-root.keystore -srcalias rootca/v2 -srckeypass key-store-pass -srcstorepass key-store-pass -destalias rootca/v2 -destkeystore vvp.keystore -destkeypass key-store-pass -deststorepass key-store-pass -deststoretype PKCS12
keytool -importkeystore -srckeystore vvp-client.keystore -srcalias client -srckeypass key-store-pass -srcstorepass key-store-pass -destalias client -destkeystore vvp.keystore -destkeypass key-store-pass -deststorepass key-store-pass -deststoretype PKCS12
Generate Result Fetcher keystore
To generate Result Fetcher keystore, use the following commands:
keytool -genkeypair -alias result-fetcher.rest -dname "cn=me.result-fetcher" -validity 10000 -keyalg RSA -keysize 4096 -keystore result-fetcher-rest.keystore -keypass key-store-pass -storepass key-store-pass
keytool -exportcert -keystore result-fetcher-rest.keystore -alias result-fetcher.rest -storepass key-store-pass -file result-fetcher-client.cer
keytool -certreq -alias result-fetcher.rest -keystore result-fetcher-rest.keystore -storepass key-store-pass -file result-fetcher-client.csr
keytool -gencert -alias rootca/v2 -keystore vvp-root.keystore -storepass key-store-pass -ext "SAN=dns:*.job-namespace.svc" -infile result-fetcher-client.csr -outfile result-fetcher-client.cer
cat result-fetcher-client.cer vvp-root.cer > result-fetcher-chain.cer
keytool -importcert -keystore result-fetcher-rest.keystore -storepass key-store-pass -file result-fetcher-chain.cer -alias result-fetcher.rest -noprompt
Generate Flink job keystore
To generate Flink job keystore, use the following commands:
keytool -genkeypair -alias flink.rest -keystore flink-rest.keystore -dname "CN=*.job-namespace.svc" -ext "SAN=dns:*.job-namespace.svc.cluster.local" -storepass keystore_password -keyalg RSA -keysize 4096 -storetype PKCS12
keytool -certreq -alias flink.rest -keystore flink-rest.keystore -storepass keystore_password -file rest.csr
keytool -gencert -alias rootca/v2 -keystore vvp-root.keystore -storepass key-store-pass -ext "SAN=dns:*.job-namespace.svc" -infile rest.csr -outfile rest.cer
cat rest.cer vvp-root.cer > chain.cer
keytool -importcert -keystore flink-rest.keystore -storepass keystore_password -file vvp-client.cer -alias client -noprompt
keytool -importcert -keystore flink-rest.keystore -storepass keystore_password -file chain.cer -alias flink.rest -noprompt
Import Flink job certificate into Result Fetcher keystore
keytool -importcert -keystore result-fetcher-rest.keystore -storepass key-store-pass -file flink-rest.cer -alias flink-client -noprompt
Kubernetes environment preparation
To prepare the Kubernetes environment for use, use the following command:
kubectl --namespace=vvp-namespace create secret generic vvp-keystore --from-file=vvp.keystore
The Ververica Platform configuration is provided by the values.yaml file.
vvp:
appmanager:
ssl:
keystore: /vvp-keystore/vvp.keystore
keystore-password: key-store-pass
keystore-key-password: key-store-pass
volumeMounts:
- name: vvp-keystore
mountPath: /vvp-keystore
volumes:
- name: vvp-keystore
secret:
secretName: vvp-keystore
To create Kubernetes secrets, use the following two commands:
kubectl --namespace=job-namespace create secret generic flink-truststore --from-file=flink-rest.keystore
kubectl --namespace=job-namespace create secret generic flink-keystore --from-file=flink-rest.keystore
kubectl --namespace=job-namespace create secret generic result-fetcher-keystore --from-file=result-fetcher-rest.keystore
Enable SSL for Session Cluster network communication
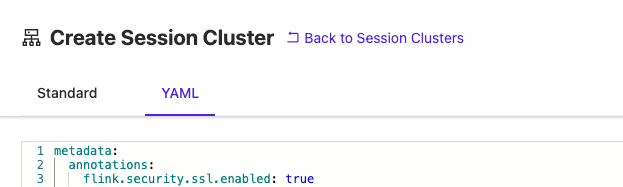
To enable SSL Session Cluster network communication, set the following property in the YAML tab:
metadata:
annotations:
flink.security.ssl.enabled: true
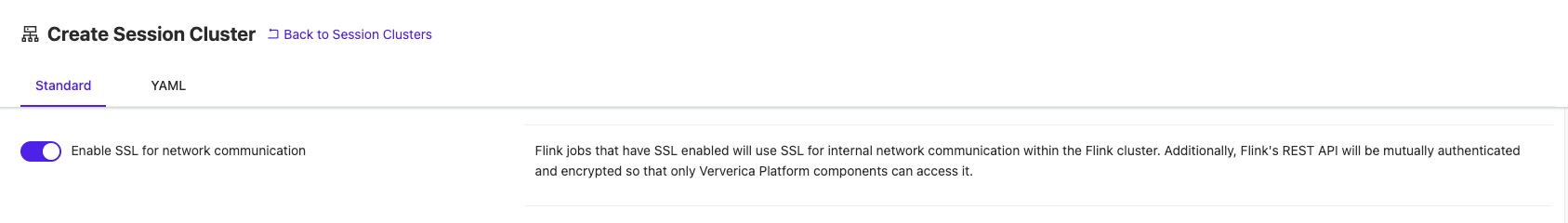
Or check the toggle in the Standard tab:
Flink configuration
To deploy the flinkConfiguration, use the following:
spec:
template:
spec:
flinkConfiguration:
security.ssl.rest.enabled: 'true'
security.ssl.rest.key-password: keystore_password
security.ssl.rest.keystore: /flink-keystore/flink-rest.keystore
security.ssl.rest.keystore-password: keystore_password
security.ssl.rest.truststore: /flink-truststore/flink-rest.keystore
security.ssl.rest.truststore-password: keystore_password
Kubernetes configuration
For the Kubernetes configuration, deploy with the following:
spec:
kubernetes:
jobManagerPodTemplate:
spec:
containers:
- name: flink-jobmanager
volumeMounts:
- mountPath: /flink-truststore
name: flink-truststore-vol
- mountPath: /flink-keystore
name: flink-keystore-vol
- env:
- name: vvp.result-fetcher.ssl.keystorePath
value: /result-fetcher-keystore/result-fetcher-rest.keystore
- name: vvp.result-fetcher.ssl.keystorePassword
value: key-store-pass
- name: vvp.result-fetcher.ssl.keyPassword
value: key-store-pass
name: result-fetcher
volumeMounts:
- mountPath: /result-fetcher-keystore
name: result-fetcher-keystore-vol
volumes:
- name: flink-truststore-vol
secret:
secretName: flink-truststore
- name: flink-keystore-vol
secret:
secretName: flink-keystore
- name: result-fetcher-keystore-vol
secret:
secretName: result-fetcher-keystore
taskManagerPodTemplate:
spec:
containers:
- name: flink-taskmanager
volumeMounts:
- mountPath: /flink-truststore
name: flink-truststore-vol
- mountPath: /flink-keystore
name: flink-keystore-vol
volumes:
- name: flink-truststore-vol
secret:
secretName: flink-truststore
- name: flink-keystore-vol
secret:
secretName: flink-keystore