Ververica Platform 2.12.1
Release Date: 2024-02-02
Changelog
Apache Flink®
Ververica Platform 2.12.1 supports the following versions:
- Apache Flink® 1.18.1
Ververica Platform 2.12.1 supports Apache Flink® 1.18 and Apache Flink® 1.17 under SLA. Apache Flink® 1.16 images are no longer provided in this version but are still supported on a best-effort basis.
For Stream Edition the following Apache Flink® Docker images are available. Please check Ververica Platform Docker Images for all available Apache Flink® images and additional tags.
- 1.16.2-stream1-scala_2.12-java8
- 1.16.2-stream1-scala_2.12-java11
- 1.17.2-stream1-scala_2.12-java8
- 1.17.2-stream1-scala_2.12-java11
- 1.18.1-stream1-scala_2.12-java8
- 1.18.1-stream1-scala_2.12-java11
For Spring Edition the following archives are available:
See Flink 1.18.1 release.
New features
Secret values for Connectors & Catalogs
Secret values are now enabled in SQL scripts and catalogs, enhancing security of sensitive information when passing credentials to connectors. Additionally, the centralized management and storage of secret values promotes consistency and credential reusability across teams.
Secret values can be accessed and created from the Administration menu under Secret Values.
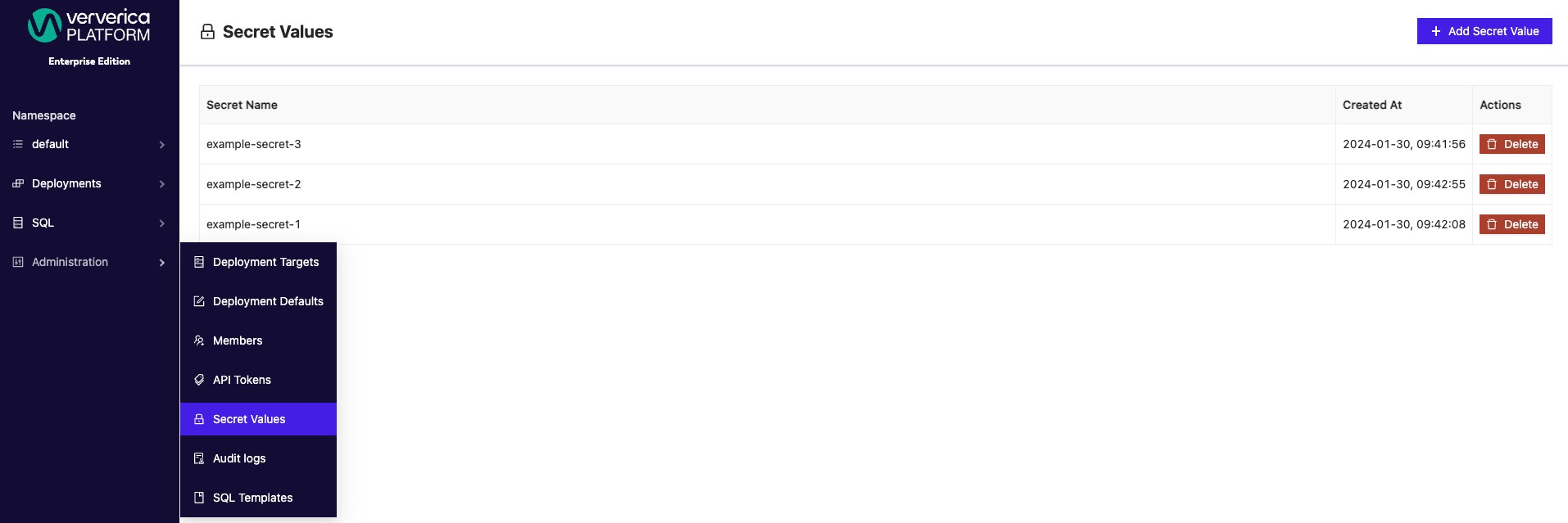
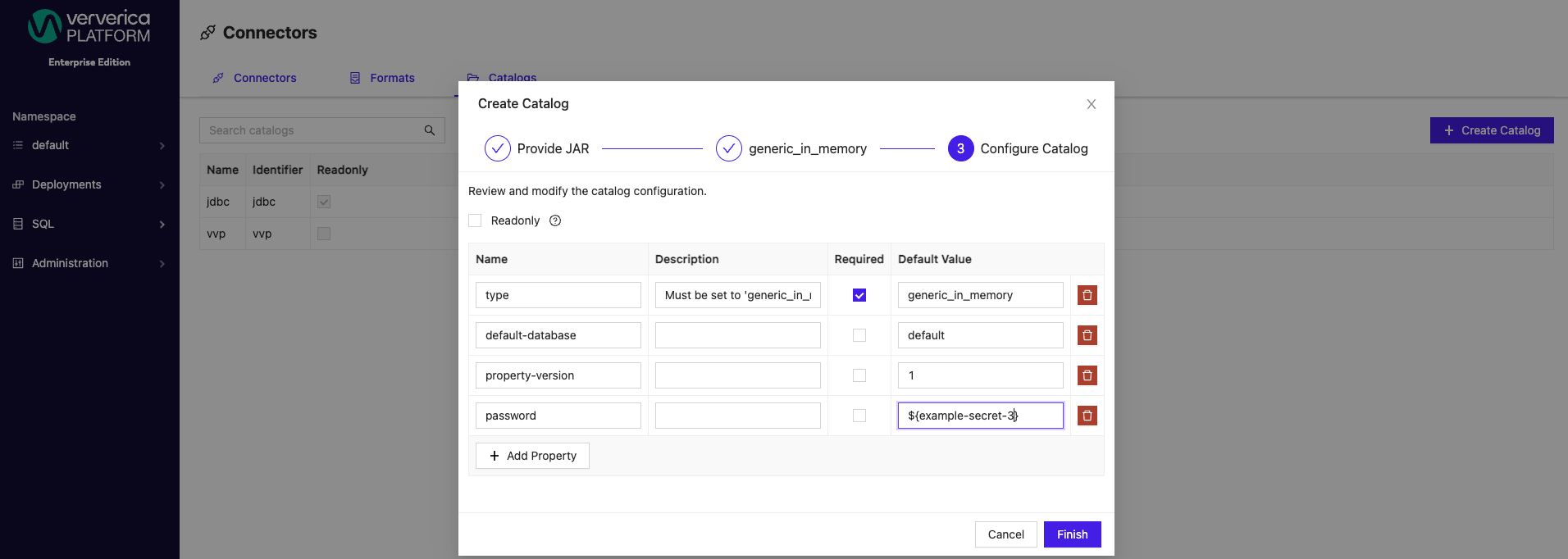
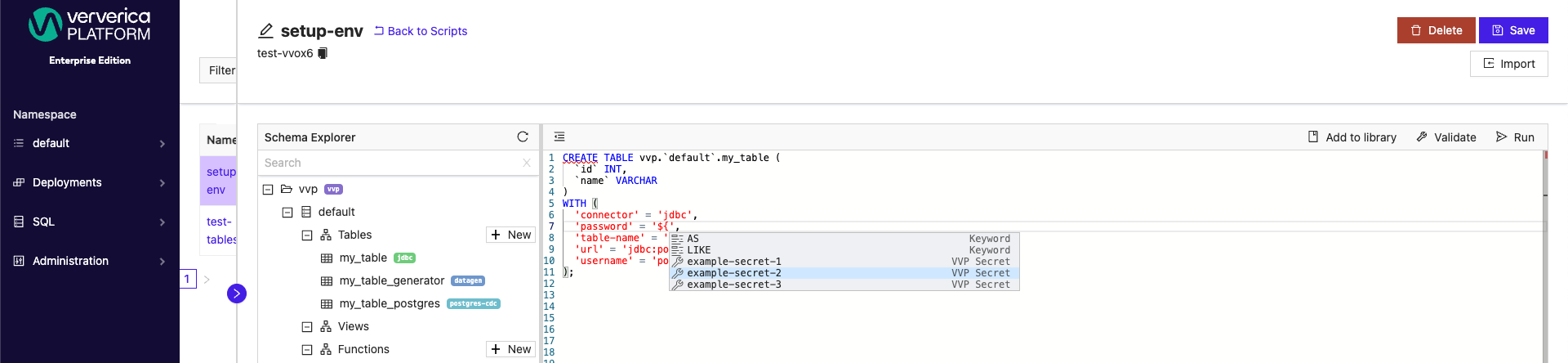
To specify a secret value, wrap an existing secret name in ${}, for example, ${example-secret}. Configured secrets can be applied as Default Values for both catalogs and connectors from the SQL menu. Secrets can be applied to both new and existing catalogs.
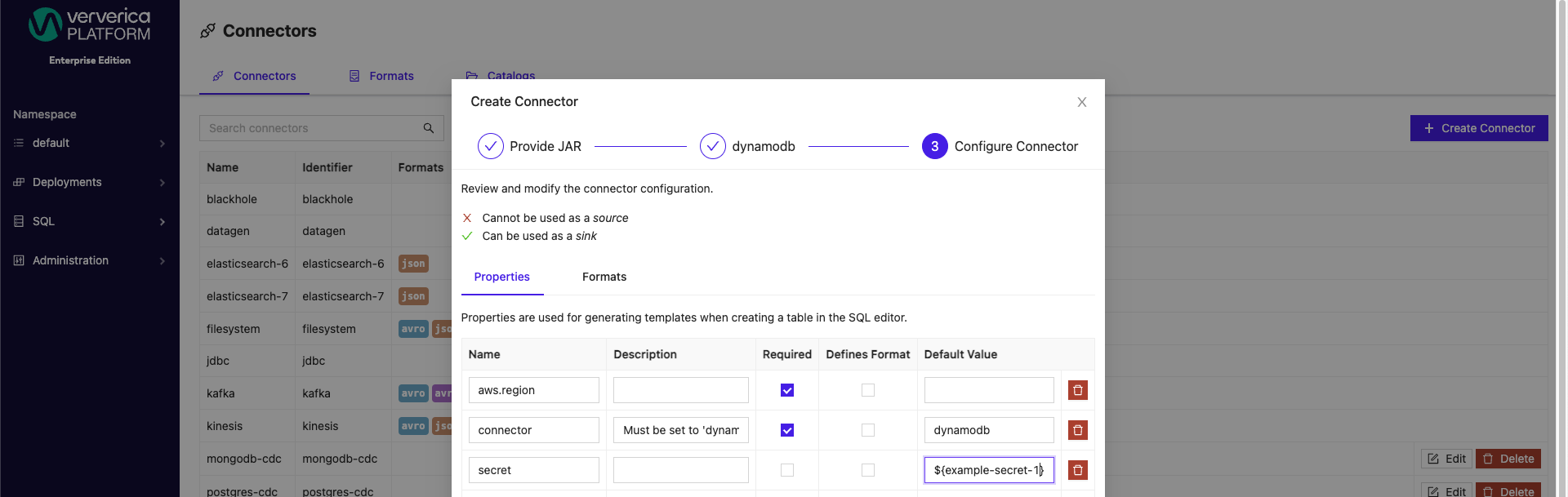
Similarly, for connectors, secrets can be applied to both new and preexisting connectors.
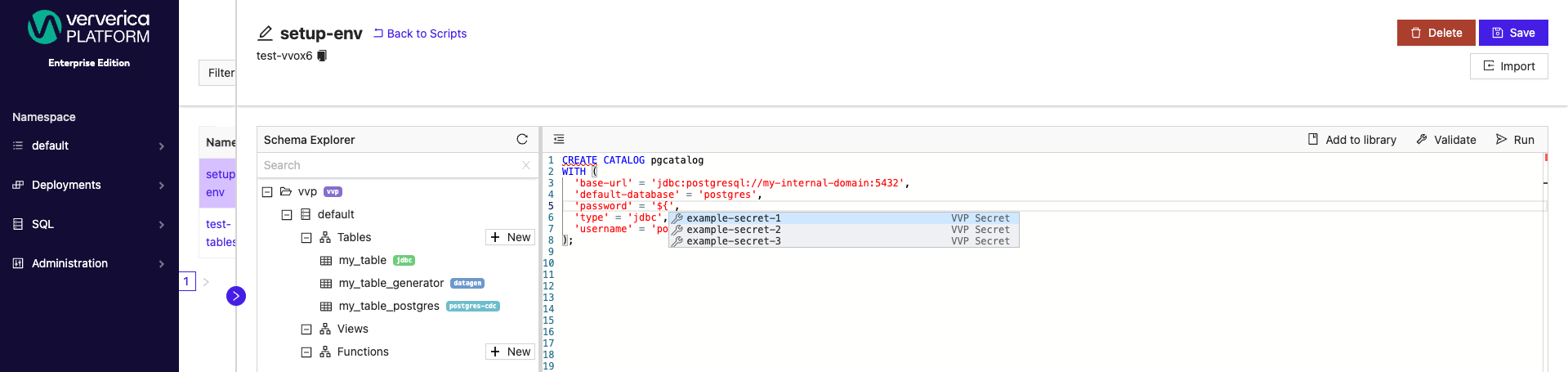
SQL Scripts can also have secret values applied when creating new or updating existing catalogs.
Additionally, new and existing tables can have secret values applied.
 .
.
In the SQL Scripts window, you can use autocomplete mechanism (typically CTRL + Space) after typing ${ to display and choose one of any existing secret names.
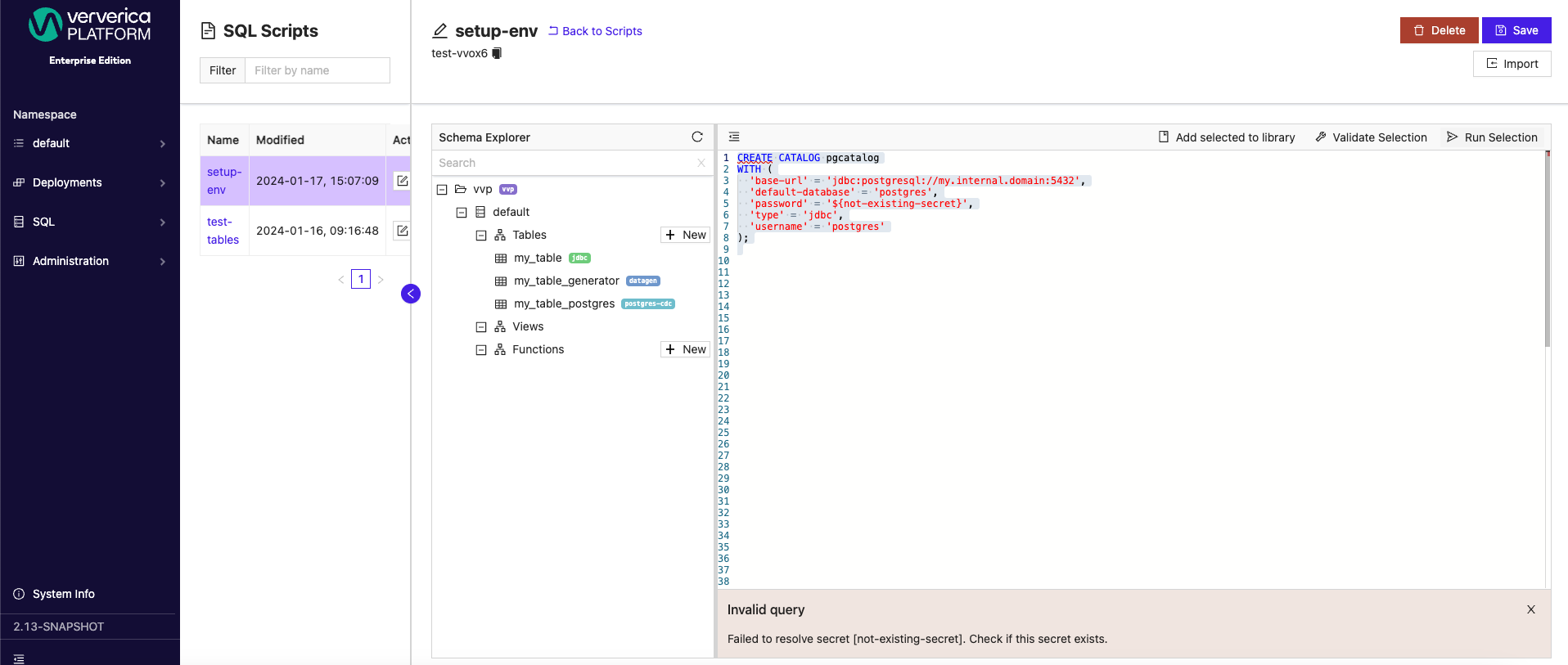
Before using a placeholder, make sure that the secret with the selected name is already created. If it does not exist, validation of the operation will fail like in the example image below.
 .
.
Improvements & Bug fixes
Audit Logs Feature Switch
With this latest release, Audit Logs are now able to be toggled on/off by admins. Toggle Audit Logs off by adding the following parameters to the Helm values.yaml file:
vvp:
auditor:
enabled: false
For more details, refer to Audit logs.
Improve SQL Script validation time
Enhanced SQL validation performance to prevent timeout errors when validating complex queries. This fix ensures a more reliable experience for large, complex SQL queries.
UI Stability improvements Post-Inactivity in VVP
In this release, we have fixed the issue where users experienced connection loss, resulting in error pop-ups, a disabled side menu, and an empty deployment list after periods of inactivity in the Ververica Platform UI. Our update now ensures a seamless reconnection to the backend without entering an error state, enhancing the stability and usability of the UI.
Cannot unregister UDF Artifact when the persistence database is MySQL
This release resolves a previous issue where users were unable to unregister UDF Artifacts when the persistance database was MySQL.
REST API returns wrong HTTP body
There was an issue where REST API calls were returning an unexpected HTTP body. This bug is now resolved and the expected JSON is returned.
Cannot Type Float Value in CPUs for Job and Task Managers
Now, it is again possible to add float values in CPUs for Job and Task Managers which was previously restricted from a recent bug.
Vulnerability Fixes (outside of Apache Flink®)
The following vulnerabilities are now removed:
-
Updated ch.qos.logback:logback-classic to resolve vulnerability CVE-2023-6378
-
Updated org.apache.tomcat.embed:tomcat-embed-core to resolve vulnerability CVE-2023-46589
-
Updated io.projectreactor.netty:reactor-netty-http to resolve vulnerability CVE-2023-34062
-
Updated org.webjars.npm:swagger-ui-dist to resolve vulnerability CVE-2018-25031
-
Updated com.amazonaws:aws-java-sdk-bom to resolve vulnerability CVE-2024-21634
-
Updated io.awspring.cloud:spring-cloud-aws-dependencies to 3.0.4
-
Updated gRPC to 1.58.0
-
Updated Spring Boot version to 3.1.8
Upgrade
As always, we recommend upgrading via Helm using the following commands:
$ helm repo add ververica https://charts.ververica.com
$ helm repo update
$ helm upgrade [RELEASE] ververica/ververica-platform --version 5.8.1 --values custom-values.yaml